Cyber Insurance - What does cyber insurance covers?
1. Introduction
As Robert Mueller (FBI Director 2012) put it: “There are only two types of companies: those that have been hacked and those that will be”

Virtually every business relies on data and computer systems. When these systems experience a virus or other computer attack (cyber attack), a business is at real risk of losing critical information that is essential to daily operations and potentially exposing itself to third-party liability. Since data can be sold at extremely high prices in the black market, hackers have strong motivation to hunt after these data.
Statistics show that for companies that they were hacked in the past, there is a 65% possibility for them to be re-hacked in the future.
In 2018 the Cyprus Government will have to fully comply with the Personal Data Protection Policies and the newly established institution of the Commissioner for Personal Data Protection will be fully activated. This practically means that during information leakage, all companies are obliged to inform not just the Authorities of Data Protection but also all of their clients, employees, suppliers, etc. who were directly or indirectly involved in the leakage.
The Cyber Insurance helps clients prevent and safeguard against sensitive data breaches, computer hacking, employee error and more.
2. Who can hack your company and how?
Even if your company applies the most stringent security policies and uses the most advanced firewall software, the danger still lurks. Cybercrime is the most rapidly evolving crime industry in the world.
2.1. Most likely categories of hackers
- Spy Hackers. Corporations hire hackers to infiltrate the competition and steal trade secrets. They may hack from the outside or gain employment in order to act as a mole.
- Black Hat Hackers. Threats to disclose data or attack a system to extort money. Extortion of data and the consequent close to the “black cyber-market”.
- Young hackers.
- State-sponsored hackers.
- Dissatisfied Employees. Usually, employees can use sabotage in order to destroy the files of the company.
- Hacktivists.
The usual methods hackers are using to steal data are:
- Antenna Devices
- Internet.
- Phishing e-mails to steal your passwords and have access to your server.
- USB Devices.
Tools hackers use to achieve their aims:
- They can install malware components or malicious programs to your computer (viruses, worms, Trojan, Trojan spyware).
Some of these malicious programs cannot be detected because of they:
- use exploits and a rootkit component
- mimic security software to evade detection
- mimic legitimate windows services
3. The most likely targets
All companies possessing data like names, addresses, bank accounts, credit cards or personal information of clients face a significant risk of being hacked.
- Clinics, Hospitals: They face significant risk due to leakage of sensitive information on clients’ medical history and social security numbers. Also, they face significant risk from competitors.
- Financial Institutions
- Corporate Service Providers
- Web hosting companies
- On-line shops
- Educational institutions: They possess credit card numbers of students, their grades, medical history, etc.
- Legal companies that possess data on their customers.
Small businesses are even more likely to be hacked since they have limited security and technical resources. Light security makes them easy targets.
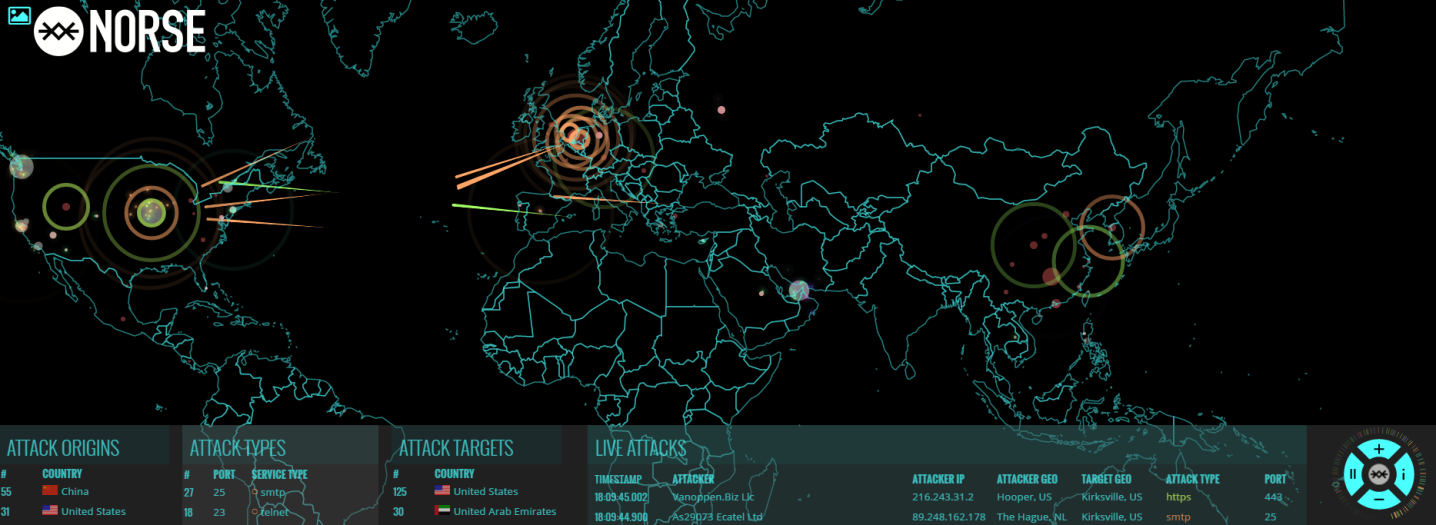
As the Norse Attack Map (map.norsecorp.com) shows, companies from all over the world are attacked on a daily basis.
4. The most famous Cyber-attack case in Cyprus
In 2014 one of the most prestigious corporate service providers in Cyprus become a victim of a Cyber-Attack orchestrated by one of the most notorious hackers in the world. The hacker phoned the director of the company demanding a ransom of €10.000.000 in bitcoins. He said that he possessed Sensitive Data of the company’s clients and that in case his demands were not met, he would release them resulting in incalculable damages for both company and clients. The director was not convinced, but 10 minutes later he received stolen personal data on his computer. Immediately the director communicated with our partners in order to handle the crisis. A crisis management was called in order to deal with the crisis, while NYA experts come from London in order to proceed with ransom negotiations. The IT consultants were able to detect that the hacker had inserted a USB in a computer connected with the network of the company 2 years ago, thus extracting data of two Gigabytes. The NYA managed to reduce the ransom fee from Ƀ € 10,000,000 to Ƀ € 900,000 but the company finally agreed to pay Ƀ € 1,100,000. The payment will be made in a period of 6 years.
5. A loss for the company
The direct damage of the company is:
Economic loss due to the halting of the company’s operations.
Crucial software programs were unavailable for days (e.g. financial company in Nicosia, loss of 35,000 euro due to the pausing of operations).
The server had to stop working until the problem was detected and solved.
Significant economic damage for the restoration of data.
Loss of data e.g. personal data, sensitive data that might help competitors (e.g. pricing policy, operating expenses, the contact information of clients, etc)
Damage on data
Allowing attackers to view and alter the project database and information from the WinCC server.
Third party lawsuits for leakage of sensitive information of clients.
Log keystrokes to steal user credentials to bank login pages
Leaks of confidential information (e.g. 30% of the lawsuits against clinics in the USA were due to leakage of information).
Related lawsuits against the directors of the company are also covered.
Online Defamation & Copyright trademark infringement.
Hackers might find information on illegal acts (e.g. money laundering) and start threatening that the information will be disclosed to public authorities.
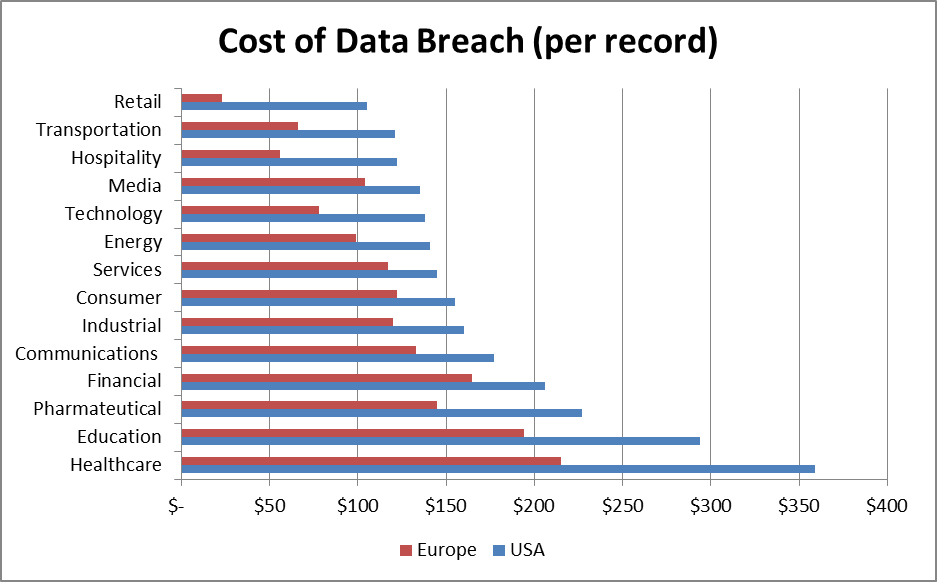
There have been many efforts to determine the real cost incurred from loss of records. In 2014 the Ponemon Institute prepared a report presenting the cost of loss for each record in the USA and Europe, with results given below (Source 2014 – Cost of Data Breach Study Global – Ponemon Institute Research Report).
6. Examples of hacking
6.1. Service Providers
- The clients of a property management firm received strange e-mail messages (with virus – attachments) that appeared to have come from the firm. An external IT consultant found that data were extorted from the company by a virus. One of the clients of the company who received the e-mail opened the virus-attachment and the result was to suffer a variety of different harms related to the virus and then incurring significant cost to have the virus removed (total cost of 50,000 euro).
6.2. Financial and Banking Institutions
- An e-mail server and external hard drive of an insured client were stolen from the premises of an outside vendor.
- The client base of an FX company in Cyprus was stolen from a competitor.
- A racket of hackers blackmailed Greek banks, including the country’s central bank, asking for bitcoin as ransom. The hackers hacked the systems of three banks and caused a few minutes of interruption of transaction. Then they communicated with the Central Bank authorities saying that the interruption was just a token of their abilities and that they could significantly damage the banking transaction systems if their demands were not met.
6.3. On-line sales
- Hackers attacked an online sales business with malware. The operations of the company were ceased for one month. Extensive IT work was required in order to regain control of the site, and a significant amount of business was lost while the work progressed (total cost 45,000 euro).
6.4. Clinics
- In Valencia, Spain a major clinic hired a hacker to destroy the archives of a smaller clinic.
7. Coverage
The policies of Pitsas Insurances provide broad affordable cyber liability protection, specifically designed for the needs of your business to address the ever-growing thread of information security exposures.
7.1. Coverage of the Cyber-Attack Insurance
The coverage includes the following categories of expenses:
- Cost for the assessment of the problem (forensics)
- Cost of a Crisis Management Expert
- Cost of informing affected clients.
- Fines and sanctions against the company
- Legal Advice.
- Cost of the negotiator in the cases the hacker requires a ransom
- Payment of Ransom. Our company cooperates with the global negotiations expert company NYA International which consists of former army officers and special agents.
- The cost associated with computer restoration
- Data recollection, recovery from electronic resources
- Data recreation from non-electronic sources
- Public Relationship (PR) company that will help you to rebuild your reputation.
- Third party liability
In case an employee causes a problem to the software or to the database deliberately, then the insurance policy covers everything.
Conflicting cases:
- The IT of a company deliberately causes problems to the CRM system or another software program (e.g. accounting) rendering it useless. The insurance company is not clear whether it will pay the cost for the acquisition of new software beyond the cost for the restoration of the data.
7.2. The limits of traditional insurance contracts
- The Public Liability Insurance contract provides coverage against economic loss occurred by a third party, excluding data breach.
- The Professional Indemnity Insurance is limited in the provision of coverage against errors, omissions and wrongful acts committed during your usual professional practice.
- The traditional Property Insurance exclusively covers economic loss from natural causes and not from Cyber attacks.
8. Additional Insurance Policies
8.1. Crime Insurance
The Cyber Edge insurance is usually combined with Crime Insurance (our package is called CrimeGuard Choice).
8.1.1. Coverage Highlights
- Provides coverage for loss of money resulting from employee theft, a fraudulent act committed by any other person or forgery. In the case of our contract, the meaning of employee is expanded to include: full-time, part-time, director, officer, independent contractor, etc.
8.1.2. Claims Scenarios
- A manager signs off fraudulent invoices
- A contractor steals (pilfers) property from your client’s premises.
- An employee forges credit card receipts.
- Impersonation Fraud (Fake President Fraud): When a person pretends to be a senior-level group executive in order to fraudulently initiate a payment.
9. Protect your business from a Cyber Attack
9.1. Data Protection Policy
- Ask a lawyer to create a data protection policy for your company.
- All the employees should be provided with a copy and be informed of any update of the company’s data protection policy.
- In case you have a data protection policy you should review it with the guidance of a lawyer and an IT specialist.
To get a calculation of the cost of insurance, follow the link Cyber Insurance.
Pitsas Insurances,
03/07/2019